A weakness of an asset or group of assets that can be exploited by one or more threats
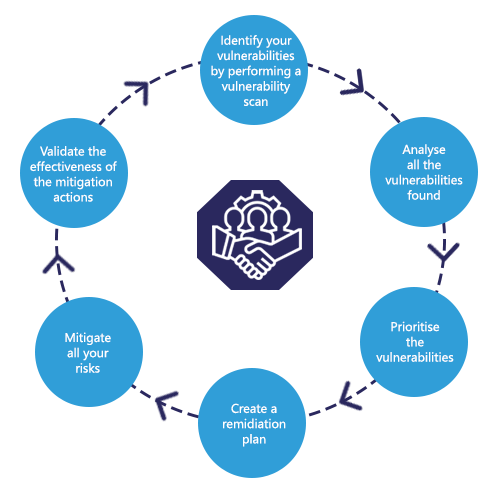
Vulnerabilities exist in almost all modern software either as software bugs or as configuration issues. ISO 27002 standard defines vulnerability as “A weakness of an asset or group of assets that can be exploited by one or more threats”. Exploiting known vulnerabilities is one of the greatest security threats. To keep your organization secure from exploitation, you have to proactively keep track of the updates and manage your patches. Hundreds of patches are released every day. How do you keep up with large amounts of patch releases? How do you prioritize which patches and updates are the most critical?
A vulnerability management process is imminent to an organisation to control security risks. Today’s threat landscape is different to that of a few years ago, thousands of vulnerabilities are reported daily. Most organizations perform vulnerability scans quarterly or on an annual basis. You lose visibility on any vulnerability found in between the period of your last scan to your next scan, leaving your organization at risk and vulnerable to attackers.